How to Add Firewall Rules in Plesk: A Comprehensive Guide
Securing your server is crucial to maintaining the integrity and performance of your web applications. One effective way to enhance your server’s security is by configuring firewall rules. If you’re using Plesk, a popular web hosting control panel, adding and managing firewall rules is a straightforward process. In this guide, we’ll walk you through the steps to add firewall rules in Plesk, ensuring your server is protected from unauthorized access while allowing legitimate traffic.
What is a Firewall?
A firewall acts as a barrier between your server and the outside world, controlling incoming and outgoing traffic based on predetermined security rules. It helps block malicious traffic while allowing legitimate connections, thereby safeguarding your server from potential threats.
Why Use Plesk’s Firewall?
Plesk provides a built-in firewall management tool that simplifies the process of adding and managing firewall rules. Using Plesk’s firewall feature, you can:
- Control Access: Define which IP addresses or ranges can access your server.
- Protect Services: Specify rules to allow or block traffic for different services (e.g., HTTP, FTP, SSH).
- Customize Rules: Create tailored rules to meet your specific security needs.
Steps to Add Firewall Rules in Plesk
1. Log in to Plesk
Begin by logging into your Plesk control panel. You’ll need administrative access to configure firewall rules.
2. Navigate to the Firewall Settings
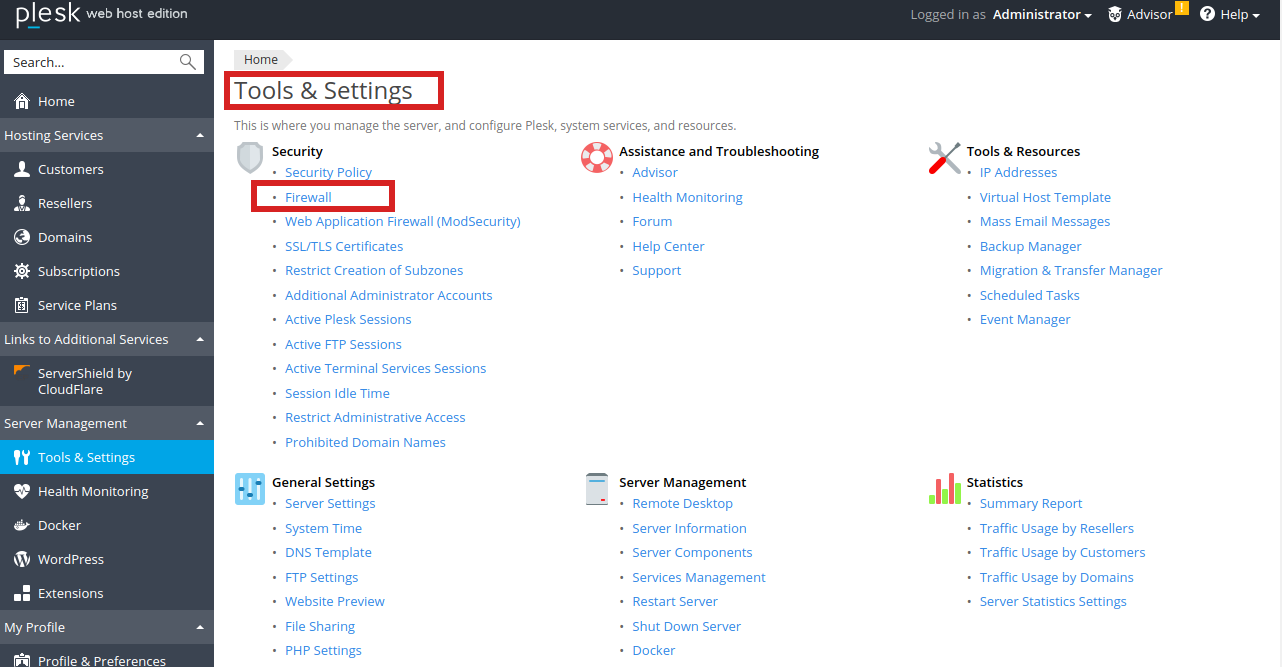
- Go to Tools & Settings: On the left sidebar, click on “Tools & Settings.”
- Find Firewall Settings: In the “Security” section, click on “Firewall.”

Add Firewall Rules in Plesk
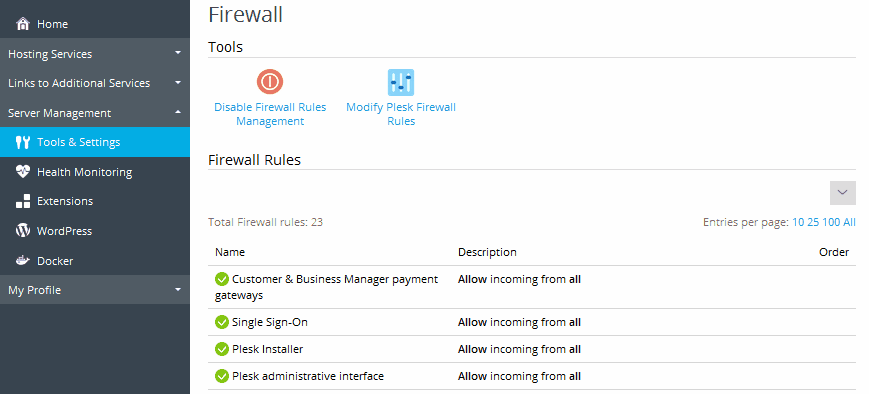
3. View Existing Rules
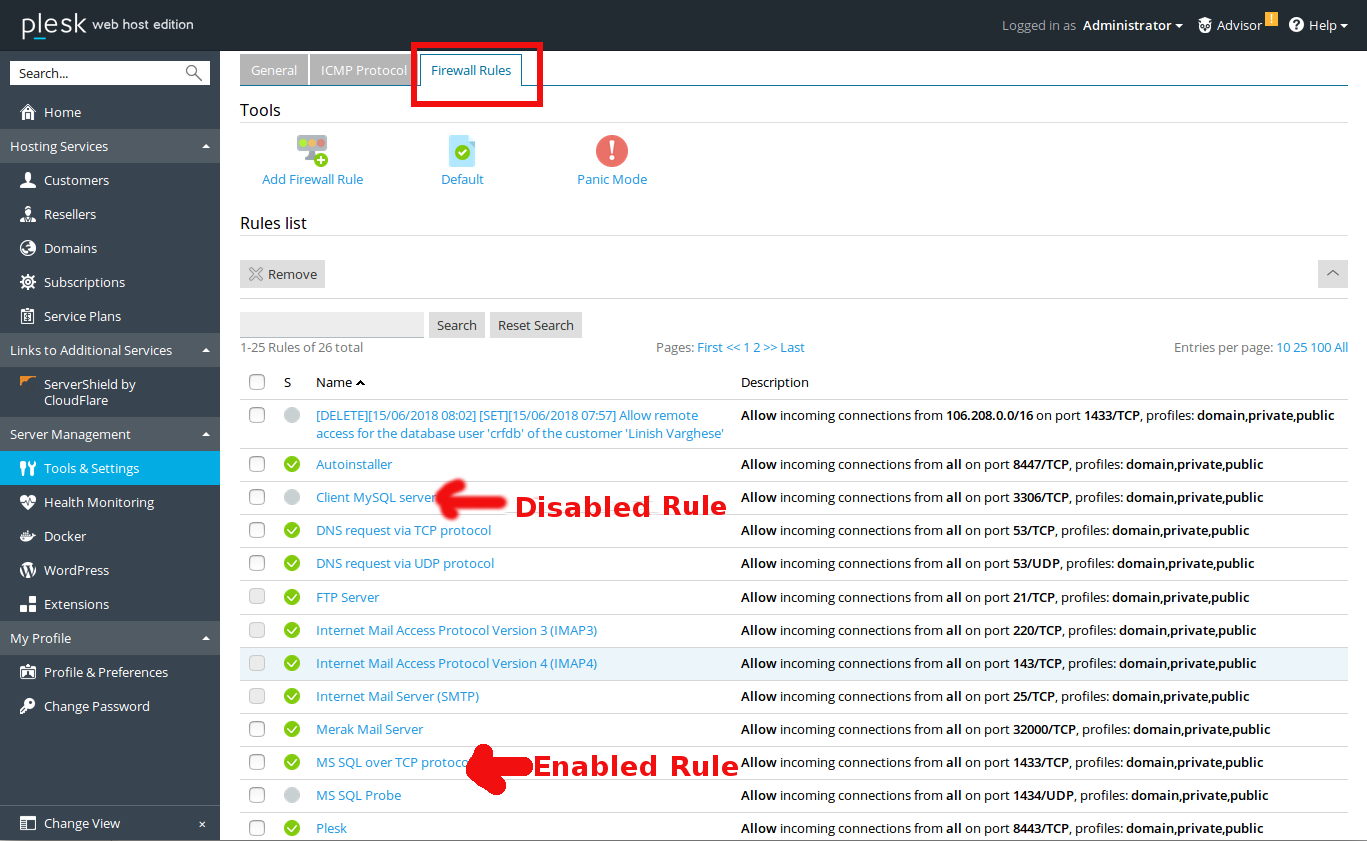
In the firewall settings, you’ll see a list of existing rules. You can review these rules to understand your current firewall configuration.
4. Add a New Rule
- Click on “Add Rule”: Look for an option to add a new rule, usually found at the top of the list or in a menu.
- Define Rule Parameters:
- Rule Action: Choose whether the rule will “Allow” or “Deny” traffic.
- Protocol: Select the protocol (e.g., TCP, UDP) for the rule.
- Port Range: Specify the port or range of ports this rule applies to.
- Source IP: Define the IP addresses or ranges that this rule will apply to. You can choose to apply the rule to all IPs or specify particular addresses.
- Destination IP: Optionally, you can specify the destination IPs if you want to restrict traffic to certain addresses.
- Add Rule Description: It’s a good practice to add a description for each rule, detailing its purpose (e.g., “Allow HTTP traffic from all IPs”).
- Save Changes: Once you’ve configured the rule, click “OK” or “Save” to apply the changes.
5. Review and Test Rules
After adding your rules, review them to ensure they are correctly configured. Test your server’s accessibility based on the new rules to verify they’re functioning as expected.
6. Monitor Firewall Logs
Regularly check firewall logs to monitor traffic and identify any potential issues. Logs can provide insight into blocked attempts and help you fine-tune your firewall rules.
Best Practices for Firewall Rules
- Least Privilege Principle: Only allow the minimum amount of access required. For example, if only one specific IP should have access to a particular service, configure the firewall rule accordingly.
- Regular Updates: Periodically review and update your firewall rules to adapt to new security threats or changes in your network environment.
- Backup Configurations: Before making significant changes, backup your current firewall configuration to avoid accidental lockouts.
Troubleshooting Common Issues
- Accidental Lockout: If you accidentally lock yourself out of your server, you may need to access it through a recovery console or contact your hosting provider for assistance.
- Misconfigured Rules: Double-check your rules if you experience connectivity issues. Ensure that the IP addresses, ports, and protocols are correctly specified.
Conclusion
Adding and managing firewall rules in Plesk is a critical aspect of server security. By carefully configuring your firewall rules, you can protect your server from unauthorized access while ensuring that legitimate traffic flows smoothly. Regularly review and update your firewall settings to maintain robust security and adapt to any changes in your hosting environment.
By following this guide, you can confidently navigate Plesk’s firewall management tools and enhance your server’s security posture. Stay proactive, and your server will remain well-protected against potential threats.